Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the sixth official challenge for DHA that was released in September of 2023.
Continue reading “DHA Challenge 2023-09 (Skyfall)”DHA Challenge 2023-06 (Solution)
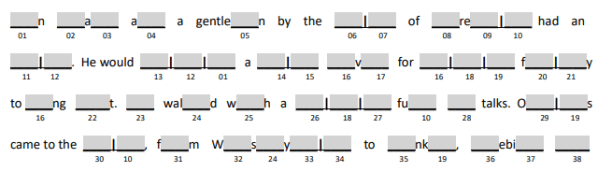
It’s been three months since the “Double Digits” challenge was released at Dallas Hacker’s Association (DHA), so it’s time to reveal the solution. If you haven’t played it yet and would like to, you can find the challenge here. Continue past the break if you’re ready to see the full solution!
Continue reading “DHA Challenge 2023-06 (Solution)”DHA Challenge 2023-08 (Billy’s Blobs)
Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the fifth official challenge for DHA that was released in August of 2023.
Continue reading “DHA Challenge 2023-08 (Billy’s Blobs)”DHA Challenge 2023-05 (Solution)
It’s been three months since the “Mystics and Magicians” challenge was released at Dallas Hacker’s Association (DHA), so it’s time to reveal the solution. If you haven’t played it yet and would like to, you can find the challenge here. Continue past the break if you’re ready to see the full solution!
Continue reading “DHA Challenge 2023-05 (Solution)”DHA Challenge 2023-04 (Solution)
It’s been three months since the “Unselected Keys” challenge was released at Dallas Hacker’s Association (DHA), so it’s time to reveal the solution. If you haven’t played it yet and would like to, you can find the challenge here. Continue past the break if you’re ready to see the full solution!
Continue reading “DHA Challenge 2023-04 (Solution)”DHA Challenge 2023-07 (Musical Mysteries)
Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the fourth official challenge for DHA that was released in July of 2023.
Continue reading “DHA Challenge 2023-07 (Musical Mysteries)”DHA Challenge 2023-06 (Double Digits)
Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the third official challenge for DHA that was released in June of 2023.
Continue reading “DHA Challenge 2023-06 (Double Digits)”DHA Challenge 2023-05 (Mystics)
Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the second official challenge for DHA that was released in May of 2023.
Continue reading “DHA Challenge 2023-05 (Mystics)”DHA Challenge 2023-04 (Unselected Keys)
Each month I create a new challenge for the Dallas Hacker’s Association (DHA) that involves elements of logic puzzles and cryptography, and award some prize to whomever first solves it. I have decided to start posting those challenges to this site as well for those who either can’t attend or want to play remotely. I will then provide the solutions to the challenges three months later in a separate article. This was the first official challenge for DHA that was released in April of 2023. Good luck!
Read more: DHA Challenge 2023-04 (Unselected Keys)You can find the challenge here.
Dallas Hacker’s Association – 2023-01-04
If you attended my talk at DHA tonight and are looking for the slides, please find them here!