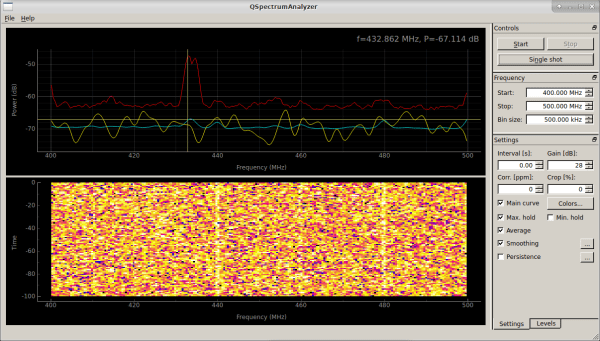
I have to teach some folks how to find, isolate, and analyze signals tomorrow, which of course means this is the perfect time to document some quick steps for my own reference. I started the build out from the DEFCON 26 Hardware Hacking Village Kali Live Build. If you don’t have it your mileage may vary… on to the buildout.
DEFCON 26 Badge Photos
I’ve been taking photos of all the badges/SAOs/Challenge Coins/etc I collected at DEFCON 26. I’m sure I’ve missed a few, but in no particular order here are the images so far, with a quarter for size reference. I’ll be making very high resolution images of most in the future, but now these will work.
Backpack Pentesting
I made a presentation a few months ago based on a simple question I relieved… “What is all that stuff in your backpack?” I normally carry, well, more than I really need. Full list with links is below, or here’s the presentation for those who want to see it in all its original, horrible glory. Ever wonder what types of stuff I normally carry when on a pentest? Well, now you know. Enjoy!
Chuck Lumley
I maintain a modified version of Kali I use as the basis for my testing which includes a variety of extra tools, preference, references, etc. If you want a copy yourself, you can find one here:
https://drive.google.com/drive/folders/1id6hRacVUtcQRtq8zjSkxtTSE3AvxTk3?usp=sharing
Each version is named for a different character played by Henry Winkler, for the record.
Introduction to Hardware Protocols
As you begin diving into hardware hacking and reading printed circuit boards (PCB) you will likely come across several common protocols. This article isn’t intended to be an exhaustive list of content, but rather a quick guide to identifying which protocols are commonly used, what they require, and what common tools will let you interface with them. I’ll be covering the following protocols in this article:
- RS-232
- USB
- I2C
- SPI
- JTAG
- UART
- USART
Benedict Slade
I maintain a modified version of Kali I use as the basis for my testing which includes a variety of extra tools, preference, references, etc. If you want a copy yourself, you can find one here:
https://drive.google.com/open?id=1X0IHNuRCWjHoQdvQUaEwWoDLKEB1_5ti
CTF-Tools
I’ve started tracking individual CTF and other tools that I typically add to distributions to my standard GitHub. If you want/need to pull any of these they are located here:
Identifying JTAG
This is a quick-hit post because as I’ve been working on some hardware hacking efforts I realized that while there are a lot of good resources on identifying JTAG interfaces and standards, there wasn’t really a good single page view of them. With that in mind, I lifted the following images from the excellent resource at http://www.jtagtest.com/pinouts/ and put them into a single page view. Full credit to JTAGtest… I just wanted something I could quickly reference.
Intro to Cryptography (Part 3 of 3)
This is the quick-hit version of the second of three parts of Introduction to Cryptography training I gave. As with all of the formal training, you can use the below for a quick reference, or view the full presentation here.
Intro to Cryptography (Part 2 of 3)
This is the quick-hit version of the second of three parts of Introduction to Cryptography training I gave. As with all of the formal training, you can use the below for a quick reference, or view the full presentation here.