I had some requests to provide my take on the OSI model separately from the presentation I made at PwnSchool, so here you go… the most comprehensive, authoritative version of the OSI model ever presented.
Wireless Hacking
This is just a quick post to provide the presentation I gave tonight at PwnSchool. If you’d like to review it you can download it here. Thanks!
Topics covered:
- Introduction to Radio Frequency
- Wireless Hacking (WEP and WPA2)
- RFID Hacking (HID Prox and MIFARE)
- Bluetooth Hacking (Bluelog/bluesnarfer/Wireshark/etc)
The Four Three Rule of Team PenTesting
Two posts in one night, because I’m catching up on some backlog items. I’ve been teaching/training a team on PenTesting lately, and it’s caused me to think through some personal truths and approaches that I’ve taken for several years. While going through that process I came to realize that I’d never really formally codified them; this is my attempt to do just that. It all comes down to what I’m now going to call the “Four Three Rule of Team PenTesting”.
RFID Fundamentals
I realized I didn’t have any good notes on Radio Frequency Identification (RFID) tags/badges/etc, so I figured it was time to compile that and update it while I’m at it. This post is just a quick run-down of the frequencies, types, and common cards/IDs. If you don’t know what an RFID is, for the purposes of most pentesting it’s a security badge or a key fob, like you can see in the image at the top of this posting.
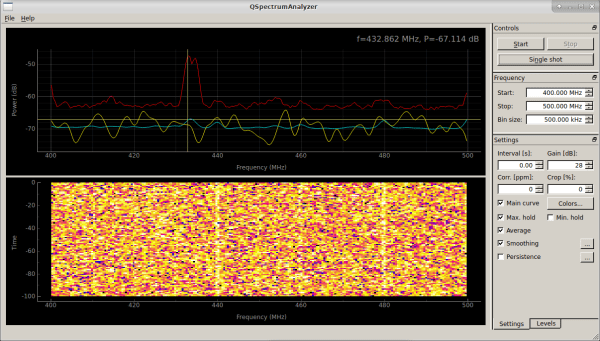
Getting Started with the HackRF
I have to teach some folks how to find, isolate, and analyze signals tomorrow, which of course means this is the perfect time to document some quick steps for my own reference. I started the build out from the DEFCON 26 Hardware Hacking Village Kali Live Build. If you don’t have it your mileage may vary… on to the buildout.
DEFCON 26 Badge Photos
I’ve been taking photos of all the badges/SAOs/Challenge Coins/etc I collected at DEFCON 26. I’m sure I’ve missed a few, but in no particular order here are the images so far, with a quarter for size reference. I’ll be making very high resolution images of most in the future, but now these will work.
Backpack Pentesting
I made a presentation a few months ago based on a simple question I relieved… “What is all that stuff in your backpack?” I normally carry, well, more than I really need. Full list with links is below, or here’s the presentation for those who want to see it in all its original, horrible glory. Ever wonder what types of stuff I normally carry when on a pentest? Well, now you know. Enjoy!
Chuck Lumley
I maintain a modified version of Kali I use as the basis for my testing which includes a variety of extra tools, preference, references, etc. If you want a copy yourself, you can find one here:
https://drive.google.com/drive/folders/1id6hRacVUtcQRtq8zjSkxtTSE3AvxTk3?usp=sharing
Each version is named for a different character played by Henry Winkler, for the record.
QuickHit: wget Website Mirroring
You may often need to mirror all (or part) of a website for offline analysis. The ‘wget’ program has some easy features to use when you want to quickly get a local copy of a site and correct common issues (like links pointing to server locations). Set up one of these behind the scenes while you work on other aspects, then peruse at your leisure.
Update 2018-07-21: Or just use the script I wrote to simplify this for my customized Kali build, available here.
TILFH: Intro to Things I Learned From Hermit
Hi there,
This is Killswitch. I’m a relatively new penetration tester trying to learn the tools of the trade. Hermit has graciously allowed me to post some guest articles from the POV of someone learning cyber security. As a newcomer to the scene, it’s easy to get overwhelmed by all of the knowledge out there in the community. My goal with these posts are to drop in little tips and tricks as I learn them from whatever source I can.
I was lucky enough to find a mentor to point me in the right direction and a community of like-minded individuals that are passionate about security in all forms. These post are my small attempt to give a little something back and try to help anyone that may be looking for a place to start learning. I hope they help.
Happy hacking,
KS